Azure Active Directory
With federated login via Azure Active Directory, you can allow your organization’s users to sign into MyEnergyCAP and EnergyCAP with their on-premises credentials. If a user doesn’t currently exist in MyEnergyCAP, a user is automatically created the first time the user authenticates. A ‘default’ role (limited permissions) is assigned to this user so it is recommend to change their permissions role to the correct role in EnergyCAP as soon as possible.
Instructions
Go to Azure Active Directory (https://aad.portal.azure.com)
Click on ‘Enterprise applications
Click on ‘New application’
Click on ‘Non-gallery application’
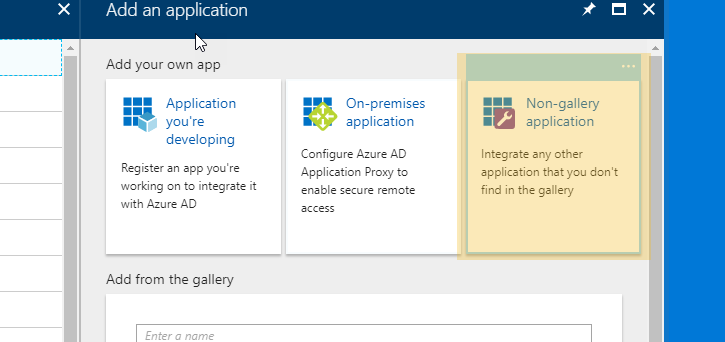
Enter ‘MyEnergyCAP’ for Name
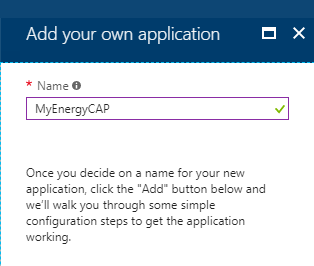
Configure single-sign on for the new application
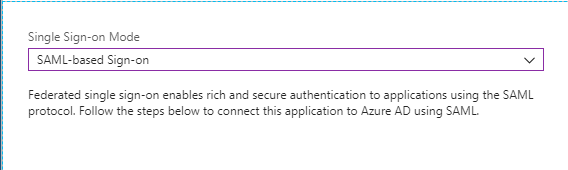
Set the Mode to ‘SAML-based Sign-on’
Set the Identifier to ‘https://auth-dev.energycap.com/auth/realms/myenergycap'
and the Reply URL to the provided URL. An example Reply URL is:‘https://auth-dev.energycap.com/auth/realms/myenergycap/broker/{id}/endpoint'
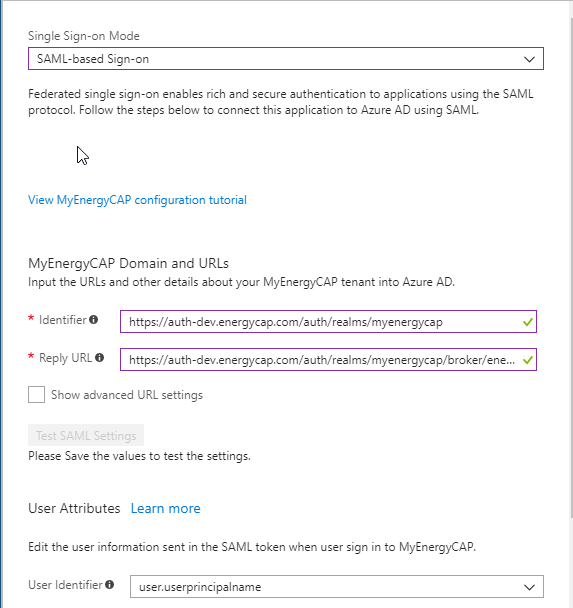
The User identifier should be set to ‘user.userprincipalname’
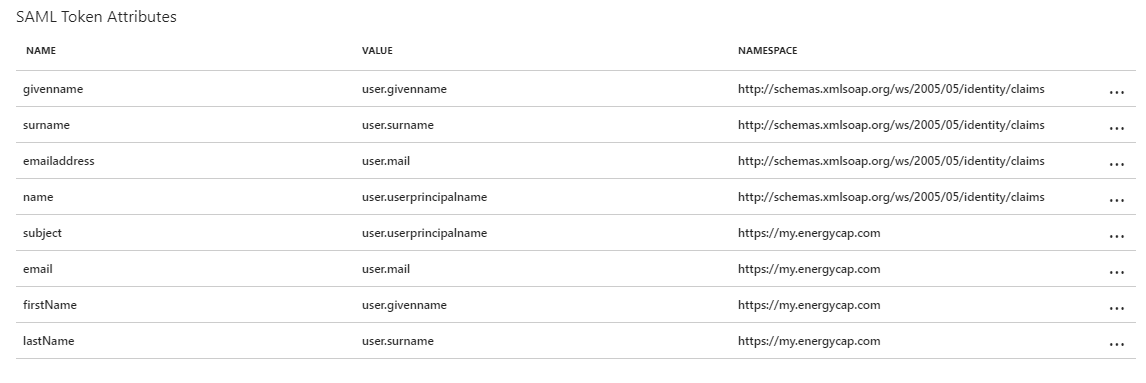
Click on ‘View and edit all other user attributes’. Add the following claims and their values:
- https://my.energycap.com/subject - user.userprincipalname
- https://my.energycap.com/email - user.mail
- https://my.energycap.com/firstName - user.givenname
- https://my.energycap.com/lastName - user.surname
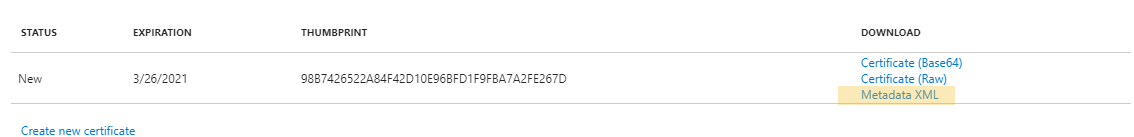
Create a new certificate if one is not active
Download the Metadata XML and forward this to your EnergyCAP project manager